
This is part 2 of compliance and user governance. Here is part 1.
Attack simulator is a tool for educating users and gathering insights on what they do wrong or right.
Table of Contents
Who can use it?
If your organization has Microsoft 365 E5 or Microsoft Defender for Office 365 Plan 2, which includes Threat Investigation and Response capabilities, you can use Attack simulation training in the Microsoft 365 Defender portal.
| Feature | Defender for Office 365 Plan 1 | Defender for Office 365 Plan 2 | Microsoft 365 E5 / A5 Security |
| Configuration, protection, and detection | |||
| Preset security policies and Configuration Analyzer | Yes | Yes | Yes |
| Safe Attachments | Yes | Yes | Yes |
| Safe Attachments in Teams | Yes | Yes | Yes |
| Safe Links | Yes | Yes | Yes |
| Safe Documents | No | No | Yes |
| Safe Links in Teams | Yes | Yes | Yes |
| Report Message Add-In | Yes | Yes | Yes |
| Protection for SharePoint, OneDrive, and Microsoft Teams | Yes | Yes | Yes |
| Anti-phishing policies | Yes | Yes | Yes |
| Real-time reports | Yes | Yes | Yes |
| Advanced protection for internal mail | Yes | Yes | Yes |
| Automation, investigation, remediation, and education | |||
| Threat Trackers | No | Yes | Yes |
| Campaign Views | No | Yes | Yes |
| Threat investigation (advanced threat investigation) | Real-time detections | Explorer | Explorer |
| Automated investigation & response | No | Yes | Yes |
| Attack simulation training | No | Yes | Yes |
| Integration with Microsoft 365 Defender | No | Yes | Yes |
So it’s on premium feature, but nice to have premium feature.
What you can do Attack Simulator?
With attack simulator you can create payloads and run them against your user base. The following payloads are currently available.

You will covering Drive-by URL in my examples. Drive-by URL is an attack type that presents you with link that forwards to an malicious web page.
What is Drive-by URL?
Drive-by URL is also knows as watering hole attack or drive by attack.
It can also be combined with Credential harvest to get get access to your identity and access to your files.
Quicktip! Use MFA for securing your identity against any wrong doer. MFA prevents 99,9% of the identity thefts.

How to create a payload?
So back to Drive-by attack. When you create an payload you can choose different types of emails from the template gallery

Or copy them to your own payload template.

When you copy you can choose different only Email for now, but hopefully in the future Microsoft will bring the other payloads also to Attack Simulator as they are also used widely by people inside Evergreen Microsoft 365 services.

So you can configure the template as you see fit for your company requirements.
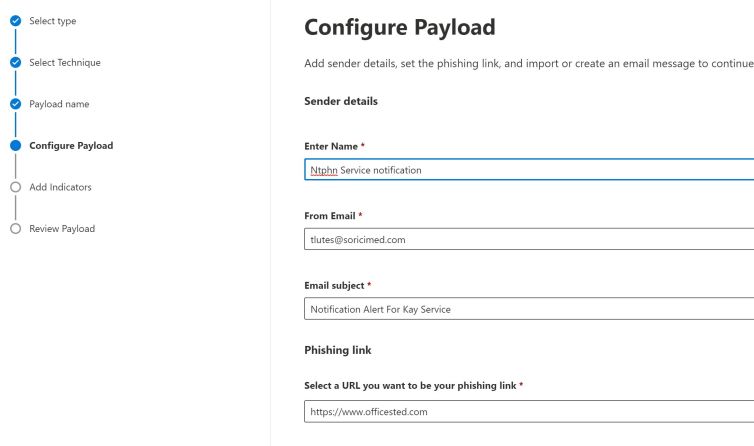
And add Email template or modify inside the portal.

Then you will add and verify indicators to educate the users. Indicators will help employees going through the attack simulation understand the clue they can look for in future attacks.

And then you can send test or preview the email that will be sent.

When you send the email it will inform you that it’s only for test and will not be included in simulation reporting.

And what the email look like for the user.

Running a simulation
When you have payloads configured and tested you can start planning the simulation. You select the payload that you made or from templates. In here you can still edit the payload and send a test.

Then you will target users. Note that Guest users are automatically excluded from the simulations.

And then you can let Microsoft assign training based on the user actions on the simulation. How cool is that!

And finally the landing page when things go wrong with the user. But like it says; “It’s okay! You’re a human”

Then configure the days for it to run.

And review the simulation at the end. And you can again send a test before enabling.

Getting insights from users
In the Simulation page you can see your simulation and the settings that you defined.

When you open it you will the details and of course a hook as it is phishing.

So that was a tiny part of Attack Simulator. It’s an excellent tool to educate and gather insights based on user actions. And also gives user governance for the company. It’s not all about technology, it is also about user education and keeping vigilant against the evolving threats.
Here’s more information about Attack Simulator Training

Stay tuned and safe out there!

 RSS - Posts
RSS - Posts