
Continuing the journey with Defender for cloud. This time we will see Data source, how to onboard Azure resources and Azure ARC integration.
With the exponential rise of cloud services, companies now place a high priority on protecting cloud workloads. For safeguarding your cloud workloads, Microsoft Defender for Cloud offers a complete solution. Finding the data sources that Microsoft Defender for Cloud should be ingesting is crucial for ensuring the greatest protection. We’ll go through how to locate these data sources in this blog article, as well as the significance of security center partner integration.
Table of Contents
Identify data sources to be ingested for Microsoft Defender for Cloud
Think about the many types of cloud services your company use to determine the data sources that should be consumed for Microsoft Defender for Cloud. Examples of data sources that should be consumed for Microsoft Defender for Cloud include the following:
Azure logs
- Azure activity logs: These logs are crucial for keeping track of resource settings and consumption since they provide details about Azure resource management procedures.
- Azure Active Directory logs: These logs record user and group administration actions and are crucial for spotting account breaches and insider threats.
Seem from from Audit logs here.

And for Sign-in logs here

Retention times
| Report | Azure AD Free | Azure AD Premium P1 | Azure AD Premium P2 |
|---|---|---|---|
| Audit logs | Seven days | 30 days | 30 days |
| Sign-ins | Seven days | 30 days | 30 days |
| Azure AD MFA usage | 30 days | 30 days | 30 days |
And there are those retention period, so do export them to Azure Monitor s or to your favorite external SIEM. Otherwise during the breach, you will be blind as a bat.

Infrastructure
- The flow logs from the Azure Network Security Group: These logs include details on incoming and outgoing network traffic and may be used to spot unwanted network activities.
- Virtual machine logs: You can spot suspicious behavior on your virtual machines by using these logs to track virtual machine activities.

What else you should monitor?
- Monitor suspicious activities from administrative accounts.
- Monitor the location from where Azure resources are being managed.
- Monitor attempts to access deactivated credentials.
- Use automated tools to monitor network resource configurations and detect changes.
Microsoft has a framework called WAF. There are several best practices that you can follow, including the topic in mention.

Partner solutions
And you also have power of Partner solutions if Azure doesn’t offer all that you need or you just have a third-party solution to monitor and collect those logs. Microsoft isn’t jealous from that choice, it’s all up to you.
- Partner solutions: Defender for Cloud’s deployment of Azure security solutions automatically connects them. Other security data sources, such as on-site or cloud-based computers, can be connected. Because most security providers forbid external agents from operating on their appliances, Defender for Cloud does not deploy the Log Analytics agent on partner virtual appliances.

If you want to send your logs to External SIEM, this is what the process look like. Microsoft will use Event Hub to send the content to your SIEM solution. Just as a side note that with Event Hub you can also receive content from different solutions to Azure. Not the topic of this series but maybe in the future. I deal with a lot of different solutions that don’t have anything to do with security but as we can see it all ties together in some form or another.

You can learn from this Microsoft article

Configure automated onboarding for Azure resources
Automation is always nice to have in place, it takes the possibility of human errors from the map.
A number of additional security capabilities are available when Defender for Cloud is enabled.
You are a part of the security operations team, You are in charge of making sure the workloads are secured by Microsoft Defender for Cloud and offering alternatives for unprotected workloads.
So let’s discover how this can be achieved. First navigate to https://portal.azure.com/#view/Microsoft_Azure_Security/SecurityMenuBlade/~/EnvironmentSettings and choose you subscription(s) from the list.

And once you click it you will all the different Defender solutions that you can use and have that settings & monitoring page


To learn more on the different plans, you can this excellent Learn content from Microsoft

What happens when you enable them?
Well, all the the resources under the plan will be covered by the security features by default. Although you can disable the ones that you don’t want, remember those Azure policies that we went through in the last section of this study guide, easy as that.
One good example is those storage accounts.

Storage account have to be secure and there is excellent solution with Defender plans to do just that. Be sure to check them out if you missed them. Two different features in preview.

Connect multi-cloud and on-premises resources
Let’s show this picture again, from here you can onboard your non-Azure resources

From here you can onboard you devices and can upgrade your plan, if don’t have already have it.

And note before you begin the onboarding

See more here

So now you upgraded it and you will be able to add some resources

And here we can see the two different agents that was previously mentioned.

Azure ARC
You can manage Windows and Linux physical servers and virtual machines deployed outside of Azure, on your company’s network, or with another cloud provider using Azure Arc-enabled servers. These machines hosted outside of Azure are referred to as hybrid machines for the purposes of Azure Arc.
You can access Azure ARC hybrid server onboarding from https://portal.azure.com/#view/Microsoft_Azure_HybridCompute/HybridVmAddBlade
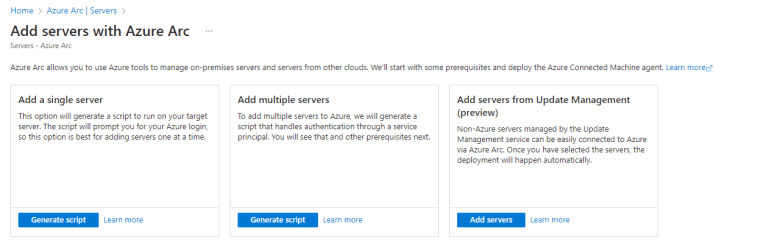
And see more on how to connect through Service principals at scale.

Or with PowerShell

Log Analytics Gateway
Download the Log Analytics Gateway to serve as a proxy if you have computers connected to your Log Analytics workspace but without internet access.
It will also support Azure Monitor, not only Log analytics, even it’s named this way.
See more from Learn

Configure data collections
In order to monitor for security flaws and threats, Defender for Cloud gathers information from your Azure virtual machines (VMs), Virtual Machine Scale Sets, IaaS containers, and non-Azure (including on-premises) devices. Certain Defender plans call for monitoring elements to gather information about your workloads.
In order to offer insight into missing updates, incorrectly configured OS security settings, the status of endpoint protection, and health and threat protection, data gathering is necessary. Only computational resources like VMs, Virtual Machine Scale Sets, IaaS containers, and non-Azure machines require data gathering.
These plans use monitoring components to collect data:
- Defender for Servers
- Azure Arc agent (For multicloud and on-premises servers)
- Microsoft Defender for Endpoint
- Vulnerability assessment
- Azure Monitor Agent or Log Analytics agent
- Defender for SQL servers on machines
- Azure Arc agent (For multicloud and on-premises servers)
- Azure Monitor Agent or Log Analytics agent
- Automatic SQL server discovery and registration
- Defender for Containers
- Azure Arc agent (For multicloud and on-premises servers)
- Defender profile, Azure Policy Extension, Kubernetes audit log data
Data collection is automatically turned on when you enable a Defender plan that requires a monitoring component.
Defender for Cloud automatically installs the Log Analytics agent on all supported Azure VMs as well as newly generated ones when automated provisioning is enabled.
And for those worrying on the billing to pile up, don’t be.

HTTP Data Collector API (preview)
You can also collect data with Data Collector API

See more here

And how to enable from Azure portal

Data collection rules
The data gathering procedure in Azure Monitor is defined by data collection rules (DCRs). DCRs outline the data that should be gathered, how it should be transformed, and where it should be sent. Azure Monitor will establish and administer some DCRs to gather a particular collection of data in order to facilitate insights and visualizations.

See more information from Learn

Closure
Some things to remember from this section.
- What are the components that you can should monitor with Defender for Cloud?
- Azure logs
- Azure AD logs
- Infrastructure and networking
- What else?
- Where to store once the retention kicks in?
- What solution should you use and what you can use?
- What about offline servers, what can be used?
- How to automatically onboard resources to Defender?
- What different onboarding solution there are?
- How to connect multi-cloud or on-premises resources?
- What resources can you connect?
- What plan use monitoring components and what happens when they are used?
That’s it, were come far on this study guide, hopefully it has been helpful so far. Until next time!
Link to main post


 RSS - Posts
RSS - Posts