
In the past years Microsoft made some excellent improvements for securing the Identity.
One of these features was Azure AD Identity Protection and it’s proxy version to allow your policies to flow inside on-premises AD.
It uses the same kinda agent than all the other Microsoft agent-based proxy services there days use. Some of these are Exchange Modern Hybrid Agent, Application Proxy, PTA Agent just to name a few.
It’s a really nice approach because you don’t have to open any ports anywhere, you just rely on Microsoft Proxy to flow the traffic to the cloud connectors.
What I have seen from Exchange and Application Proxy it works really well, there is a little bit of speed decrease on the way but it’s manageable when you compare the easy setup and debugging capabilities.
Table of Contents
Identity protection in the cloud
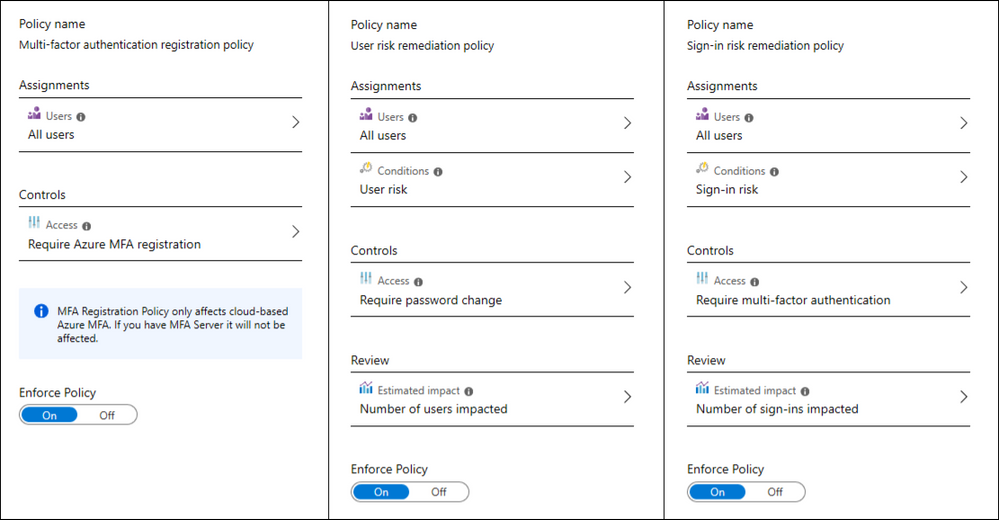
Installing Identity Protection Proxy
First you have to enable Password Writeback, it’s not mandatory just preffered because then you can use self-service password reset from the cloud but and also use the same password on-premises.

When config is done you have to run sync cycle.

Enable on-premises protection from Security -> Authentication methods and add some password that are considered bad for your organization.

Browse to https://www.microsoft.com/en-us/download/details.aspx?id=57071 and download both packages from there.


When you get them installed do a reboot and then you can check that the services are running.

There are audit and enforce modes available.
Audit mode
Audit mode is intended as a way to run the software in a “what if” mode. Each Azure AD Password Protection DC agent service evaluates an incoming password according to the currently active policy.
If the current policy is configured to be in audit mode, “bad” passwords result in event log messages but are processed and updated. This behavior is the only difference between audit and enforce mode. All other operations run the same.
Enforced Mode
Enforced mode is intended as the final configuration. Like when in audit mode, each Azure AD Password Protection DC agent service evaluates incoming passwords according to the currently active policy. When enforced mode is enabled though, a password that’s considered insecure according to the policy is rejected.
When a password is rejected in enforced mode by the Azure AD Password Protection DC agent, an end user sees a similar error like they would see if their password was rejected by traditional on-premises password complexity enforcement. For example, a user might see the following traditional error message at the Windows logon or change password screen:
“Unable to update the password. The value provided for the new password does not meet the length, complexity, or history requirements of the domain.”
This message is only one example of several possible outcomes. The specific error message can vary depending on the actual software or scenario that is attempting to set an insecure password.
Affected end users may need to work with their IT staff to understand the new requirements and to choose secure passwords.
Azure AD smart lockout
You can then enable smart lockout, but make sure that your Azure AD smart lockout duration to be higher than AD DS, then Azure AD would be 120 seconds (2 minutes) while your on-premises AD is set to 1 minute (60 seconds). If you want your Azure AD lockout threshold to be 5, then you want your on-premises AD lockout threshold to be 10. This configuration would ensure smart lockout prevents your on-premises AD accounts from being locked out by brute force attacks on your Azure AD accounts.

Lockout policy
- Open the Group Policy Management tool.
- Edit the group policy that includes your organization’s account lockout policy, such as, the Default Domain Policy.
- Browse to Computer Configuration > Policies > Windows Settings > Security Settings > Account Policies > Account Lockout Policy.
- Verify your Account lockout threshold and Reset account lockout counter after values.

Trying out Self-Service password reset
Logon to https://aka.ms/sspr

And it will offer you options to verity that you are you (of course you have MFA in-place as it will block 99,9% of phishing, right?)

So I choose Authenticator and it went thru, now it will ask the second method to verify you.

and when it finished, you done.

Easy, just easy and excellent way to keep you admins less active as they propably have other stuff to do.
That was a part of Microsoft’s large solutions pack for protecting your identity posture.
And in the next posts something else with the same topic.
over and out,


 RSS - Posts
RSS - Posts