
In the last part I explained what storage accounts are and how you can access them. In this part I will explain how to protect them from insider or external risks.
Table of Contents
Defender for storage
Azure storage accounts are billed hourly. Applies to Blob containers, File shares and Data lakes Gen2.
Threat protection alerts – Advanced behavioral analytics and the Microsoft Intelligent Security Graph provide an edge over evolving cyber-attacks. Built-in behavioral analytics and machine learning can identify attacks and zero-day exploits. Monitor networks, machines, data stores (SQL servers hosted inside and outside Azure, Azure SQL databases, Azure SQL Managed Instance, and Azure Storage) and cloud services for incoming attacks and post-breach activity. Streamline investigation with interactive tools and contextual threat intelligence.

You can find the recommendations also from Storage accounts -> Security

Explore security anomalies
When storage activity anomalies occur, you receive an email notification with information about the suspicious security event. Details of the event include:
- The nature of the anomaly
- The storage account name
- The event time
- The storage type
- The potential causes
- The investigation steps
- The remediation steps
Encryption
Storage service encryption protects your data at rest. Azure Storage encrypts your data as it’s written in our datacenters, and automatically decrypts it for you as you access it. Note that after enabling Storage Service Encryption, only new data will be encrypted, and any existing files in this storage account will retroactively get encrypted by a background encryption process.
You can encrypt your data with your own key. It can be stored in Key vault.

Networking
By default the access is allowed from all networks.
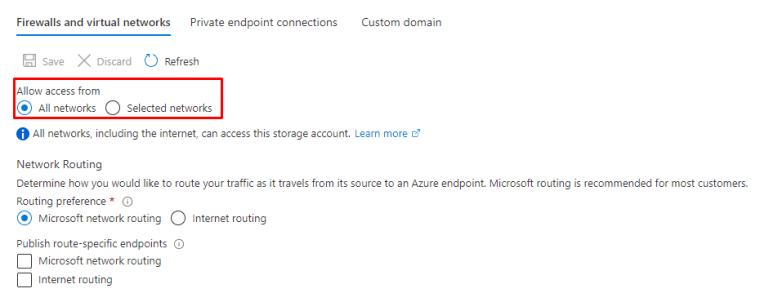
You can choose the network you have already defined or create new ones. It’s also possible to add exceptions to these rules.

Or you can use private endpoints.

The type of sub-resource for the resource selected above that your private endpoint will be able to access.

and Private Link is created.

Azure Private Link is a security feature that will flow the traffic inside Microsoft Backbone network.

Secure and public access
Disable public access if not needed and enable Secure access (https) if not already enabled. For new provisions it’s already enabled by default.

Data protection
Microsoft offers data protection controls for Storage accounts. You can find them under Data proctection.


Azure AD
Enable Azure AD authentication for Storage services. It the following I enabled it to Azure Files.

This feature is currently in Preview.

Managed identities
Use managed identities to authenticate your usage instead of normal users. You can use the below Managed identity types.

Closure
When using cloud based services it’s more and more important to close borders to your precious data. If you don’t there could serious consequences for your business or personal data.
Microsoft currently applies 126 different CIS controls to their Storage services and they keep adding more.

So, they do their part but do you?


 RSS - Posts
RSS - Posts